Quantum Computing - Looming Threat to Telecom Security
Introduction Understanding the Quantum Threat Quantum Computing Basics…
Adiabatic Quantum Computing (AQC) and Impact on Cyber
Introduction Factorization and Classical Computers Universal Quantum…
Understanding FIPS 140: A Cornerstone of Cryptographic Security
What Is FIPS 140? Why Is FIPS 140 Important? How NIST Evaluates…
Entanglement-Based QKD Protocols: E91 and BBM92
Introduction to Entanglement-Based QKD Mathematical Foundations Quantum…
Quantum Key Distribution (QKD) and the BB84 Protocol
Cryptography Background Secret or Symmetric Key Cryptography Asymmetric or…
The Quantum Computing Threat
Introduction The Breadth of the Quantum Threat to Cybersecurity and 5G…
Challenges of Upgrading to Post-Quantum Cryptography (PQC)
Introduction The Quantum Threat: A Universal Vulnerability Beyond…
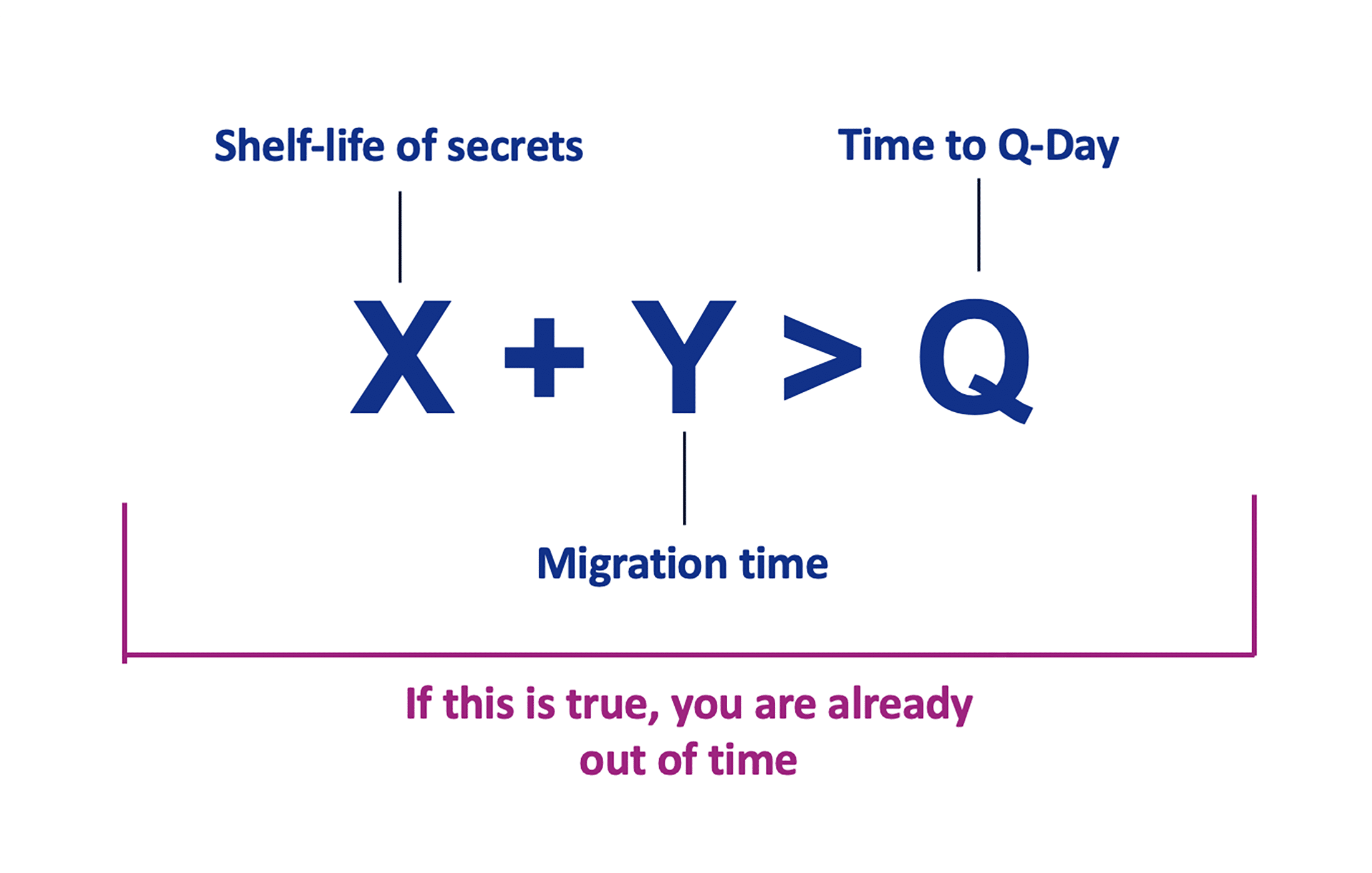
Mosca’s Theorem and Post‑Quantum Readiness: A Guide for CISOs
Introduction What Is Mosca’s Theorem? Why It Matters to CISOs The Problem…
What’s the Deal with Quantum Computing: Simple Introduction
Introduction Classical vs. Quantum Computing Superposition Exponential…