Introduction to Quantum Random Number Generation (QRNG)
Introduction The Problem with Predictability Cloudflare Lava Lamps…
Sign Today, Forge Tomorrow (STFT) or Trust Now, Forge Later (TNFL) Risk
Introduction Harvest Now, Decrypt Later vs. Sign Today, Forge Tomorrow /…
The Challenge of IT and OT Asset Discovery
Introduction Why Complete Asset Inventory Is Essential The Ever-Expanding…
Brassard–Høyer–Tapp (BHT) Quantum Collision Algorithm and Post-Quantum Security
Introduction and Overview The BHT Algorithm: Quantum Collision-Finding How…
Shor’s Algorithm: A Quantum Threat to Modern Cryptography
Introduction Background on RSA Encryption How RSA works (conceptually) Why…
Grover’s Algorithm and Its Impact on Cybersecurity
Introduction to Grover’s Algorithm Significance in Quantum Computing…
Quantum-Safe vs. Quantum-Secure Cryptography
In 2010, I was serving as an interim CISO for an investment bank. During that…
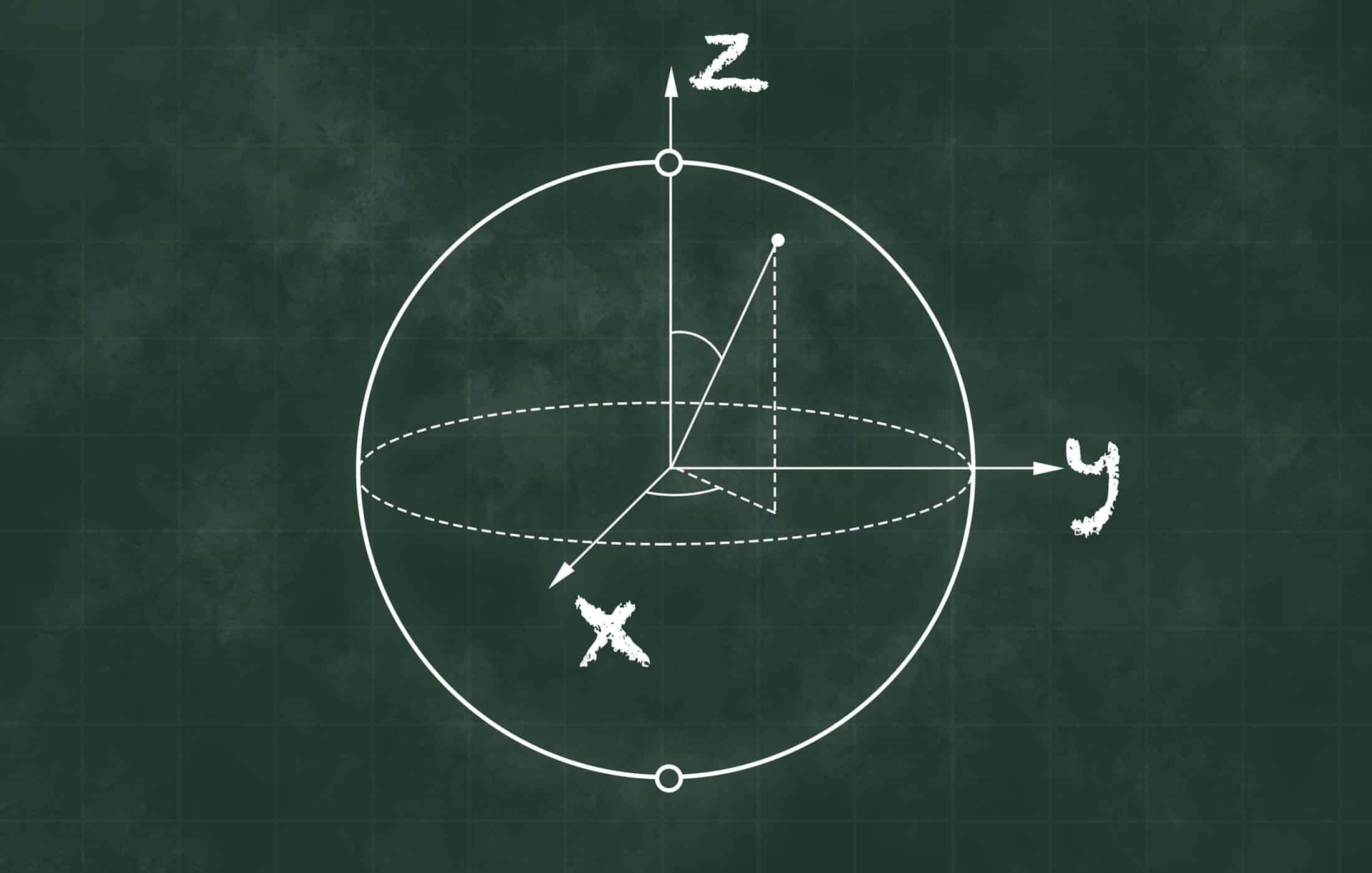
Qubits: A Brief Introduction for Cybersecurity Professionals
Introduction What Is a Qubit (and How Is It Different from a Bit)?…
Bell States: An Introduction for Cybersecurity Professionals
What Are Bell States? The Four Bell States and Notation Entanglement in…
Kuperberg’s Algorithm and its Impact on Post-Quantum Cryptography (PQC)
What Is Kuperberg’s Algorithm and What Problem Does It Solve? How Does…