Trust Now, Forge Later (TNFL) – The Overlooked Quantum Threat
What is "Trust Now, Forge Later" (TNFL)? Most discussions about quantum computing threats focus on “Harvest Now, Decrypt Later” (HNDL) - the idea that adversaries can collect encrypted data today and store it, hoping a future quantum computer will break the encryption and expose sensitive information. This risk is very real, especially for data that needs to remain confidential for decades (think government secrets, health records, long-term intellectual property). In essence, HNDL is a confidentiality threat: today’s intercepted secrets might be decrypted tomorrow. Yet there’s another quantum-enabled danger that receives far less publicity, one that worries me even more. I previously termed it “Sign Today, Forge Tomorrow” (STFT), but more recently, another, probably better term, is gaining traction: “Trust Now, ...
Quantum-Readiness / PQC Full Program Description (Telecom Example)
Preparing a large telecom (or any enterprise) for the post-quantum cryptography era is a massive, multi-faceted undertaking, but it is achievable with foresight, resources, and commitment. We’ve seen that it involves much more than just installing new algorithms - it’s about transforming an organization’s approach to cryptography across potentially thousands of applications and devices, under uncertain timelines and in coordination with many external players. In all likelihood, this quantum-readiness program will be one of the most complex IT/security projects the organization has ever executed, comparable to - or even exceeding - major transformations like the rollout of a new network generation or a large merger integration. The program spans technology, process, and people: from the nuts-and-bolts of lattice-based encryption performance, ...
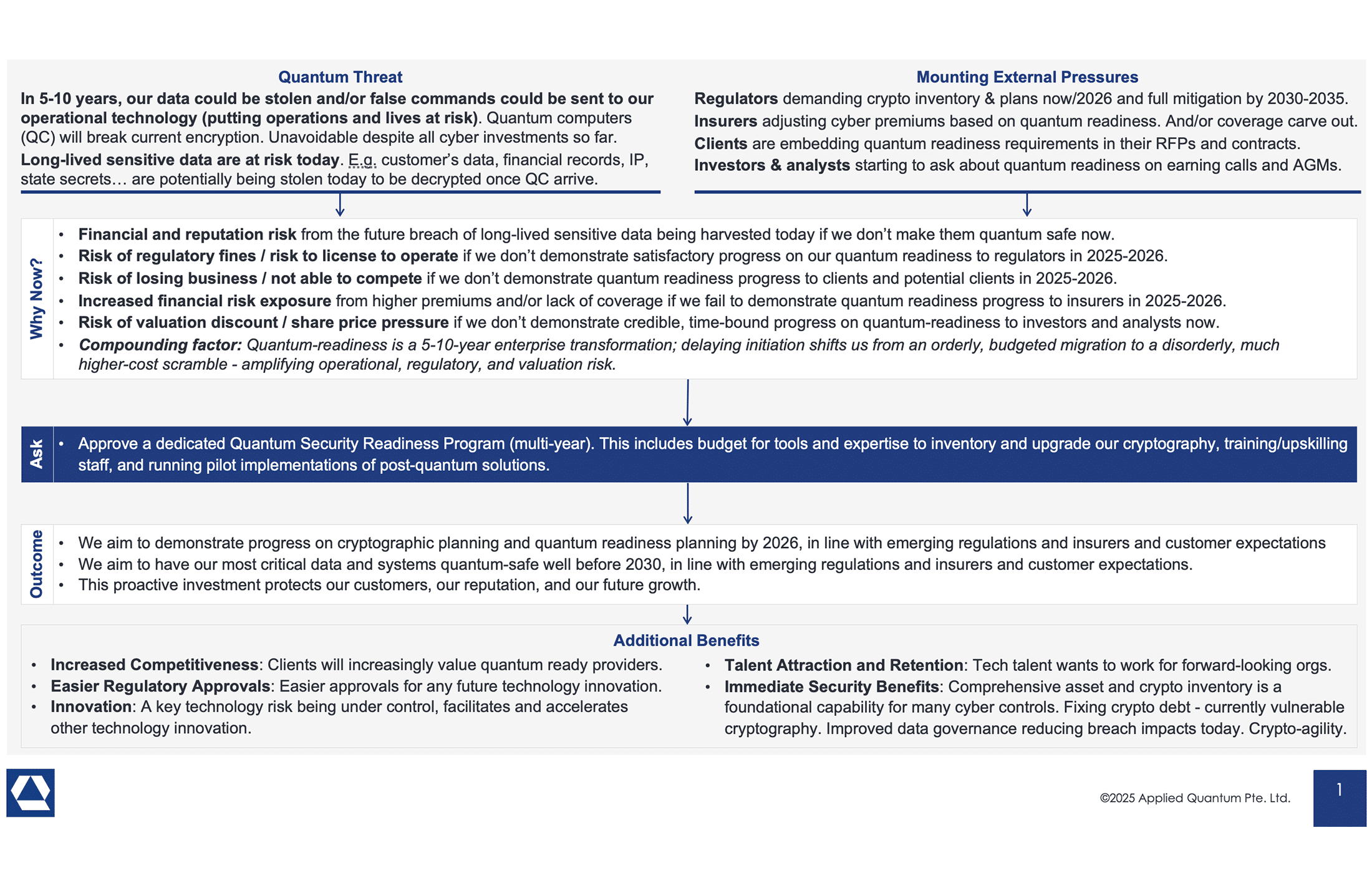
Forget Q-Day Predictions – Regulators, Insurers, Investors, Clients Are Your New Quantum Clock
Whether you personally believe Q-Day will come in 5 years or 50, the world around you isn’t taking chances - and neither can you. As a CISO, you’re now being implicitly (and sometimes explicitly) told by every corner of your ecosystem that quantum preparedness is mandatory. Regulators demand it via hard deadlines. Key clients and partners demand it in contracts and RFPs. Insurers will soon demand it as a condition of coverage. Investors and boards demand it as part of prudent risk management ...
Why Companies May Need a Chief Quantum Officer (CQO)
In my opinion, forward-thinking organizations should consider creating a Chief Quantum Officer (CQO) role. Much like those historical electricity executives, a CQO would spearhead the adoption of a disruptive technology that is revolutionary, promising - but widely misunderstood. It’s a provocative idea (even “a job title from Star Trek,” as one commentator quipped ), but it’s quickly moving from speculation to reality. A few bold companies have already appointed CQOs, signaling that quantum tech is becoming a strategic priority, not just a research experiment. I’m personally bullish on quantum’s potential, and while I expect quantum computing to become commoditized in the coming decades (eventually making a CQO as obsolete as the Chief Electricity Officer), I believe that for the next ...
Quantum Sensing and AI for Drone and Nano-Drone Detection
Quantum sensing technologies are emerging as powerful tools to detect and track UASs, including small and nano-drones that often evade conventional sensors. These quantum sensors, such as quantum radars, quantum LiDARs, atomic magnetometers, and Rydberg RF detectors, exploit phenomena like entanglement, squeezing, and extreme sensitivity of quantum states to reveal faint drone signatures beyond classical limits. However, raw data from both quantum and classical sensors can be weak, noisy, or ambiguous, especially when dealing with tiny drones with low radar cross-sections (~0.01 m²) and minimal emissions. This is where artificial intelligence (AI) becomes indispensable. Modern AI algorithms (deep neural networks, signal classifiers, data fusion models, etc.) play a critical role in processing, interpreting, and enhancing sensor signals, effectively translating subtle ...
Securing Quantum Readiness Budget Now
From a CISO and business leadership perspective, the ask is clear: we need to secure budget and resources now to begin the multi-year journey of quantum-proofing our organization. This includes funding for risk assessments, cryptographic inventory tools, new encryption software/hardware, staff training or hiring, and pilot projects to start integrating PQC. The investment is justified not only by the avoidance of a potentially catastrophic future breach, but by the immediate gains in cyber hygiene, compliance readiness, and competitive positioning that we’ve outlined. In an urgent, risk-based approach, starting early is the only viable strategy - it spreads out costs, reduces uncertainty, and ensures we won’t be caught unprepared ...
Board AI Governance and Oversight
AI is reshaping businesses across industries, and corporate boards are increasingly expected to oversee AI strategy, ethics, and risk management. In fact, the number of S&P 500 companies formally assigning AI oversight to a board committee more than tripled in 2025, and nearly half of Fortune 100 companies now highlight AI expertise in their directors’ qualifications. This surge underlines an urgent need for governance frameworks that keep pace with AI-driven innovation. Boards can no longer afford to treat AI as just an IT issue; it has become a strategic imperative - one that demands informed oversight at the highest level ...
Risk-Driven Strategies for Quantum Readiness When Full Crypto Inventory Isn’t Feasible
Given the practical challenges, organizations may need to begin their quantum-readiness journey with a risk-driven approach rather than a theoretically perfect one. The essence of this strategy is to focus limited resources where they matter most – addressing the highest quantum-vulnerability risks first and implementing interim safeguards for the rest. Even the U.S. government’s guidance recognizes the need for prioritization. For example, the federal memo mentioned above directs agencies to inventory high-impact systems, high-value assets (HVA), and any systems containing data that must remain sensitive through 2035 before worrying about less critical systems. In other words, not all cryptographic assets pose equal risk, so a sensible plan is to triage and tackle them in order of importance ...
What is the Quantum Threat? A Guide for C‑Suite Executives and Boards
Boards do not need to dive into the scientific intricacies of qubits and algorithms, but they do need to recognize that this is a strategically important risk – one that can’t be simply delegated away. It requires the same level of governance attention as other enterprise-level risks like financial compliance, geopolitical factors, or pandemic preparedness. The comforting news is that if organizations act early, the quantum threat can be managed. Think of the proactive stance many companies took with Y2K in the late 1990s – those who started early averted disaster. Similarly here, those who begin preparing for quantum now (even while the technology is still maturing) will be in the best position to avoid chaos later. Early movers might ...
How CISOs Can Use Quantum Readiness to Secure Bigger Budgets (and Fix Today’s Problems)
Quantum readiness is not an exercise in science fiction – it’s a very practical program that yields benefits immediately. Regulators are pushing us all in this direction, which means boards are willing to fund it. The journey forces you to finally catalog your cryptographic assets and clean up long-standing weaknesses, improving your security posture right now. It builds agility so you can handle any crypto curveballs the future throws. It energizes your team and attracts talent by giving them something exciting to work on. And it demonstrates to the world that your organization is on top of emerging threats, thereby inspiring confidence. For a CISO or CIO, that’s a legacy worth achieving ...
Quantum Readiness / PQC Migration Is The Largest, Most Complex IT/OT Overhaul Ever – So Why Wait?
Preparing for the quantum era is arguably the largest and most complicated digital infrastructure overhaul in history. Yes, far bigger than Y2K, because back in 1999 we didn’t have millions of network-connected “things” to worry about. Yet despite clear warnings and rapidly approaching milestones, far too many organizations still treat quantum readiness as something to punt into next year – or worse, as a simple one-click software update. It won’t be that simple. Not by a long shot. If you haven’t already started planning your post-quantum migration, you’re not just behind schedule – you may already be late ...
Cryptographic Inventory Vendors and Methodologies
Achieving a comprehensive cryptographic inventory often requires combining multiple tools and methodologies. Each solution above has blind spots: one might excel at catching code-level issues but miss network usage, another might see network traffic but miss dormant code, etc. Organizations starting a crypto inventory (especially as part of PQC readiness) should evaluate these tools in terms of their environment: for example, pairing a passive network sensor with an agent-based host scanner and a static code analyzer will cover most bases – network, runtime, and code. Many of the vendors themselves support integrations (as seen by partnerships between endpoint and network tool makers). The goal is to aggregate all findings, typically into a unified inventory database or CBOM repository, where overlapping ...