Trust Now, Forge Later (TNFL) - The Overlooked Quantum Threat
Harvest vs. Forge - Twin Quantum Threats to Security What is "Trust Now,…
Quantum-Readiness / PQC Full Program Description (Telecom Example)
Introduction Within the cybersecurity community, there is significant…
Forget Q-Day Predictions - Regulators, Insurers, Investors, Clients Are Your New Quantum Clock
The Endless Q-Day Debate For years, cybersecurity experts have debated…
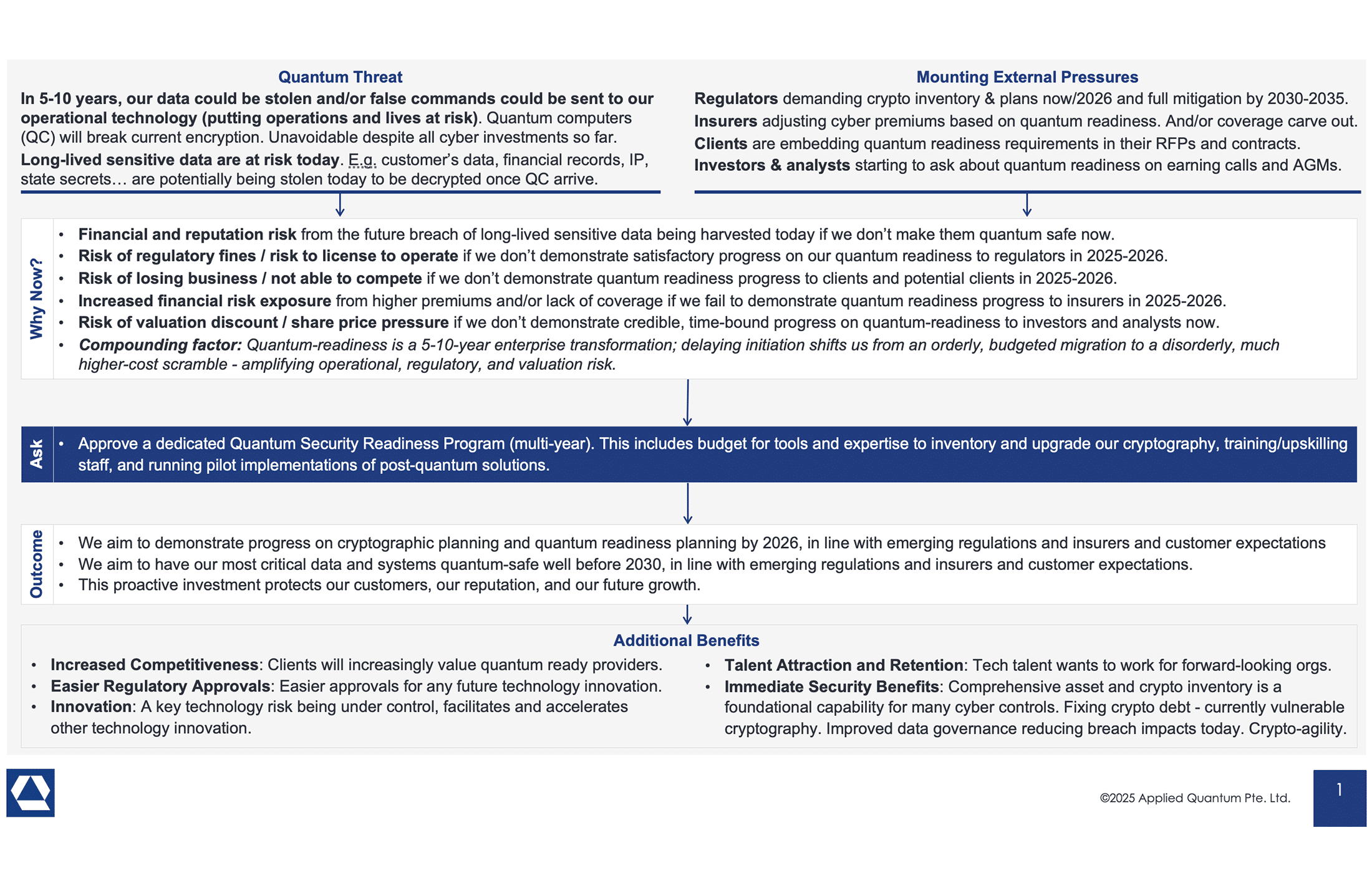
Securing Quantum Readiness Budget Now
Introduction Nearly every CISO I speak with right now is either scoping a…
Risk-Driven Strategies for Quantum Readiness When Full Crypto Inventory Isn’t Feasible
Quantum computing threatens to break or weaken today’s cryptography, putting…
What is the Quantum Threat? A Guide for C‑Suite Executives and Boards
Cybersecurity has been at or near the top of corporate risk lists for years.…
Quantum‑Readiness Programme for a Telecom Provider
Challenge A large telecommunications provider realized that preparing for the…
Quantum‑Risk and Cryptography Assessment for Interbank Payments
Challenge A coalition of financial institutions – including several major banks…
How CISOs Can Use Quantum Readiness to Secure Bigger Budgets (and Fix Today’s Problems)
Introduction Talking with the CISOs in my network, I keep hearing the same…
Quantum Readiness / PQC Migration Is The Largest, Most Complex IT/OT Overhaul Ever - So Why Wait?
Introduction Imagine an IT/OT project in which every single device,…