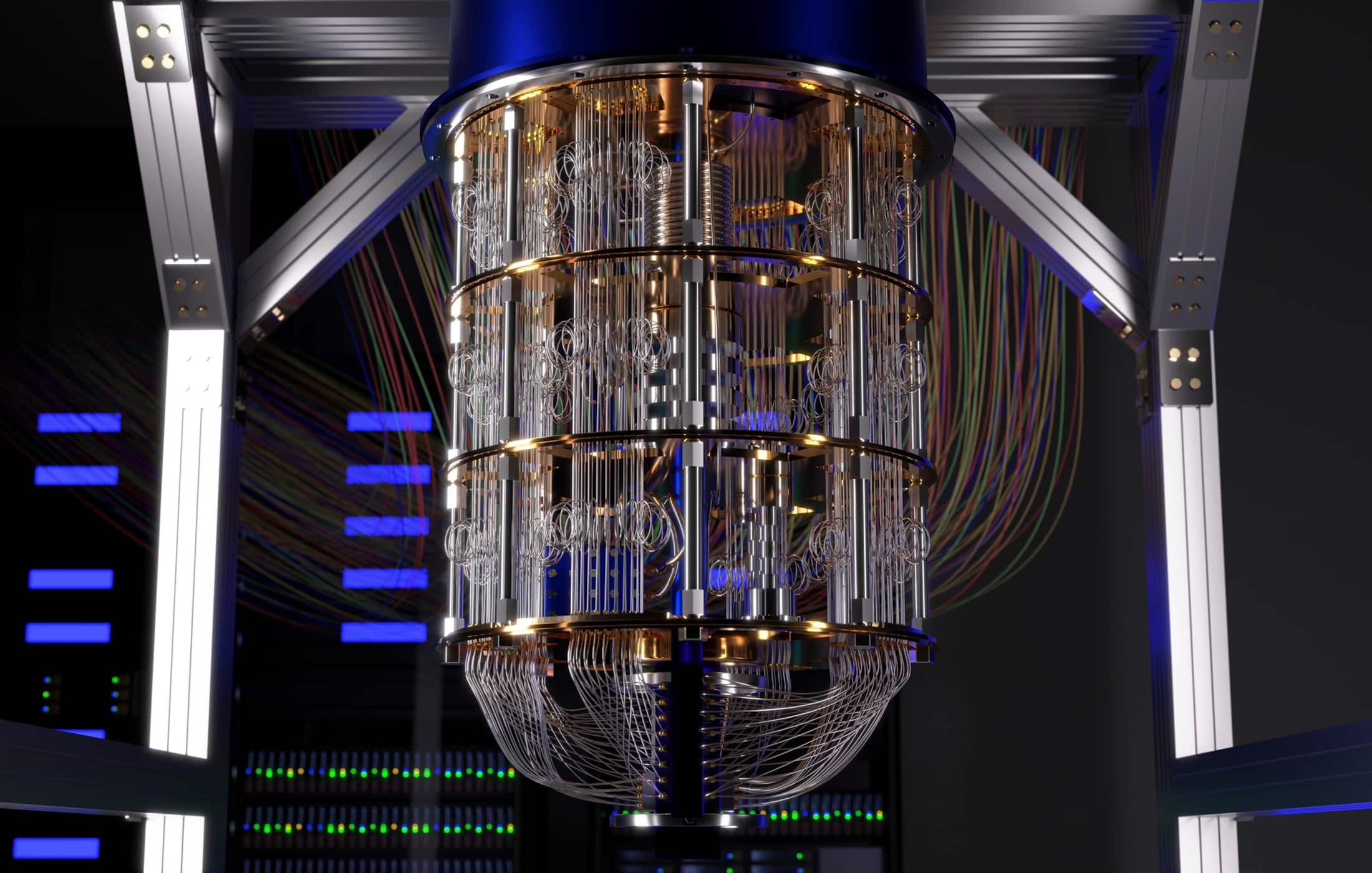
Mitigating Quantum Threats Beyond PQC
Introduction Challenges and Limitations of PQC Alternative and…
Introduction to Crypto-Agility
1. Introduction 2. Why Crypto-Agility? Why Now? 3. The Cost of Inaction 4.…
Perturbation Attacks in Text Classification Models
Introduction Text Classification Models Applications in Cybersecurity…
How Multimodal Attacks Exploit Models Trained on Multiple Data Types
The Rise of Multimodal Models What Are Multimodal Models? Why Are They…
Post-Quantum Cryptography (PQC) Introduction
Introduction How PQC Differs from Traditional Cryptography The NIST PQC…
The Threat of Query Attacks on Machine Learning Models
The Basics of Machine Learning Models The Importance of Model Security What…
Quantum Entanglement: The “Spooky” Glue Uniting Qubits and Beyond
Introduction to a Quantum Connection What Exactly Is Quantum Entanglement?…
Securing Data Labeling Through Differential Privacy
The Importance of Data Labeling Why Data Privacy Matters in Labeling…