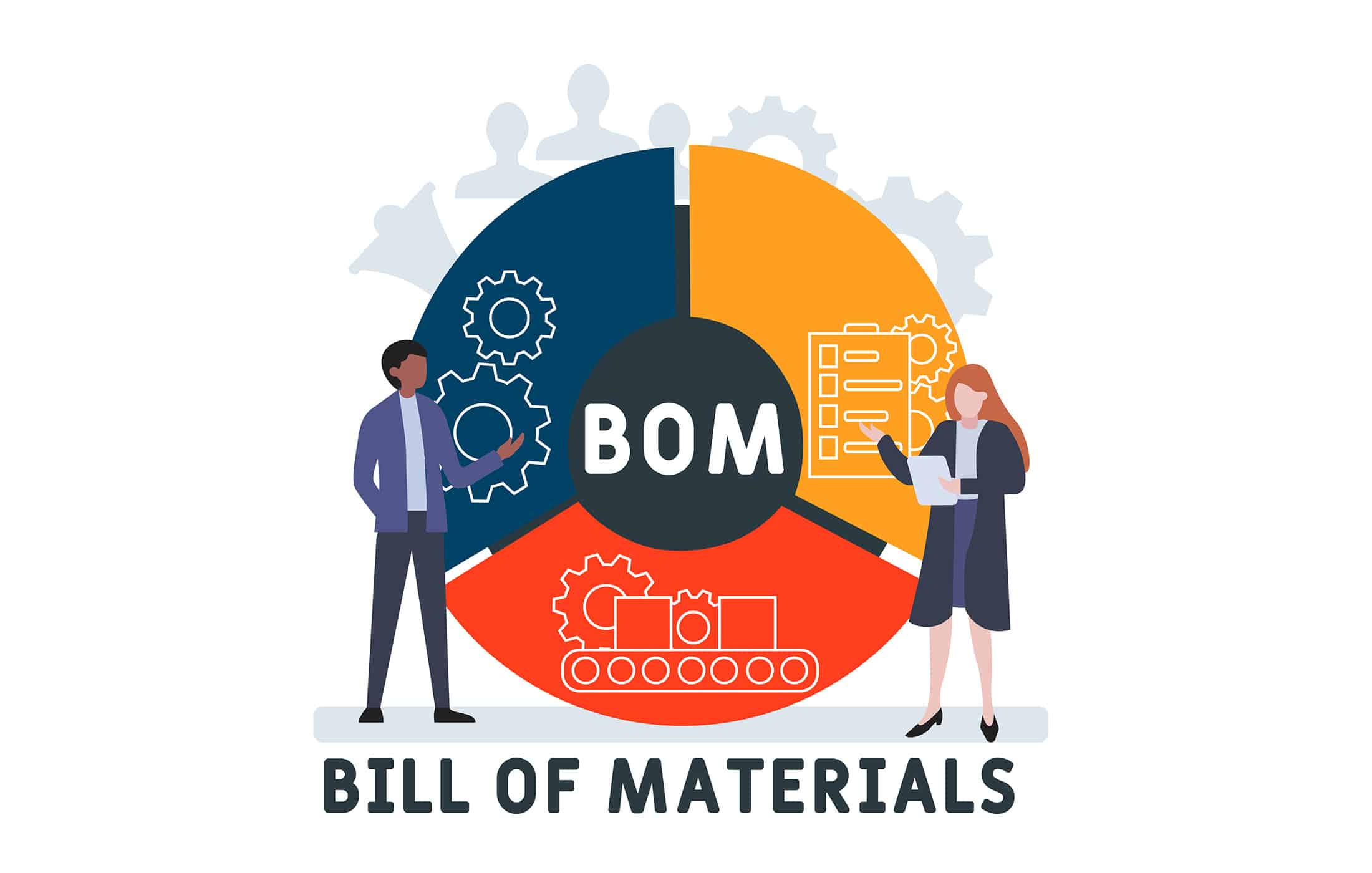
Bills of Materials for Quantum Readiness: SBOM, CBOM, and Beyond
Introduction Quantum computing threat is forcing organizations to inventory…
Inside NIST’s PQC: Kyber, Dilithium, and SPHINCS+
Introduction The race to develop post-quantum cryptography (PQC) has…
Quantum Networks 101: An Intro for Cyber Professionals
Introduction to Quantum Networks Key Technologies in Quantum Networking…
Adversarial Attacks: The Hidden Risk in AI Security
Importance of Understanding Threats in AI/ML Why Should We Care about…
Quantum Radar: The Next Frontier of Stealth Detection and Beyond
What is Quantum Radar? History and Evolution Key Papers and Experiments Use…
The Future of Digital Signatures in a Post-Quantum World
What Are Digital Signatures and Why Do They Matter? Today’s Digital…
Quantum Sensing - Introduction and Taxonomy
Introduction Theoretical Groundwork Key Challenges and Roadblocks…
Cryptographically Relevant Quantum Computers (CRQCs)
Introduction Definition of CRQC CRQC vs Early-stage (NISQ) Devices Why…
Gradient-Based Attacks: A Dive into Optimization Exploits
Introduction Understanding Gradient-Based Attacks How Gradient-Based…
Neven’s Law: The Doubly Exponential Surge of Quantum Computing
What is Neven’s Law and Where Did It Come From? Why “Doubly Exponential” Is…